From Logs to Evidence: Turning Raw Events into Compliance Ready Records
Most teams start with logs. Application logs, server logs, access logs, error logs, and monitoring logs. These logs are designed for troubleshooting and performance diagnostics, not for security investigations or compliance reporting. Yet when a security incident occurs or an auditor arrives, these same logs suddenly become the only available source of truth.
This is where most organisations run into trouble. Logs were not created to be evidence. They lack structure, integrity, and context. They are mutable and easily lost. As a result, teams struggle to produce reliable, defensible audit records that satisfy regulatory expectations.
This article explores how to bridge that gap. It explains how to transform raw, unstructured logs into meaningful, compliance ready evidence. It also outlines the principles that differentiate simple logs from robust audit trails and clarifies why many teams move from log based approaches to dedicated audit trail systems.
Table of Contents
- Why raw logs fail as evidence
- What auditors and regulators expect
- The characteristics of compliance ready audit records
- How to extract meaning from raw event streams
- Designing evidence transformation pipelines
- Immutability and hash chain guarantees
- When to centralise versus when to distribute
- Automating compliance reporting
- Building or buying an audit trail solution
- Conclusion
Why Raw Logs Fail as Evidence
Logs exist to help developers understand system behaviour. They were not created to satisfy compliance requirements. For this reason, raw logs lack several fundamentals needed for evidence handling.
First, logs are inconsistent. Each service logs in its own format, with its own naming conventions, timestamp precision, and verbosity. Trying to reconstruct a chain of events often requires correlating entries across multiple services that never agreed on a common structure.
Second, logs are mutable. They are stored in files or systems where administrators can edit or delete entries. Without strong immutability guarantees, an auditor cannot rely on them as evidence.
Third, logs lack business context. Developers write logs for developers. Key business events like customer exports, permission changes, or financial actions are often buried among debug messages and low level technical noise.
Fourth, logs are infrastructure coupled. When you scale, migrate, or rebuild systems, historical logs are lost or fragmented. Evidence should outlive infrastructure. Logs usually do not.
What Auditors and Regulators Expect
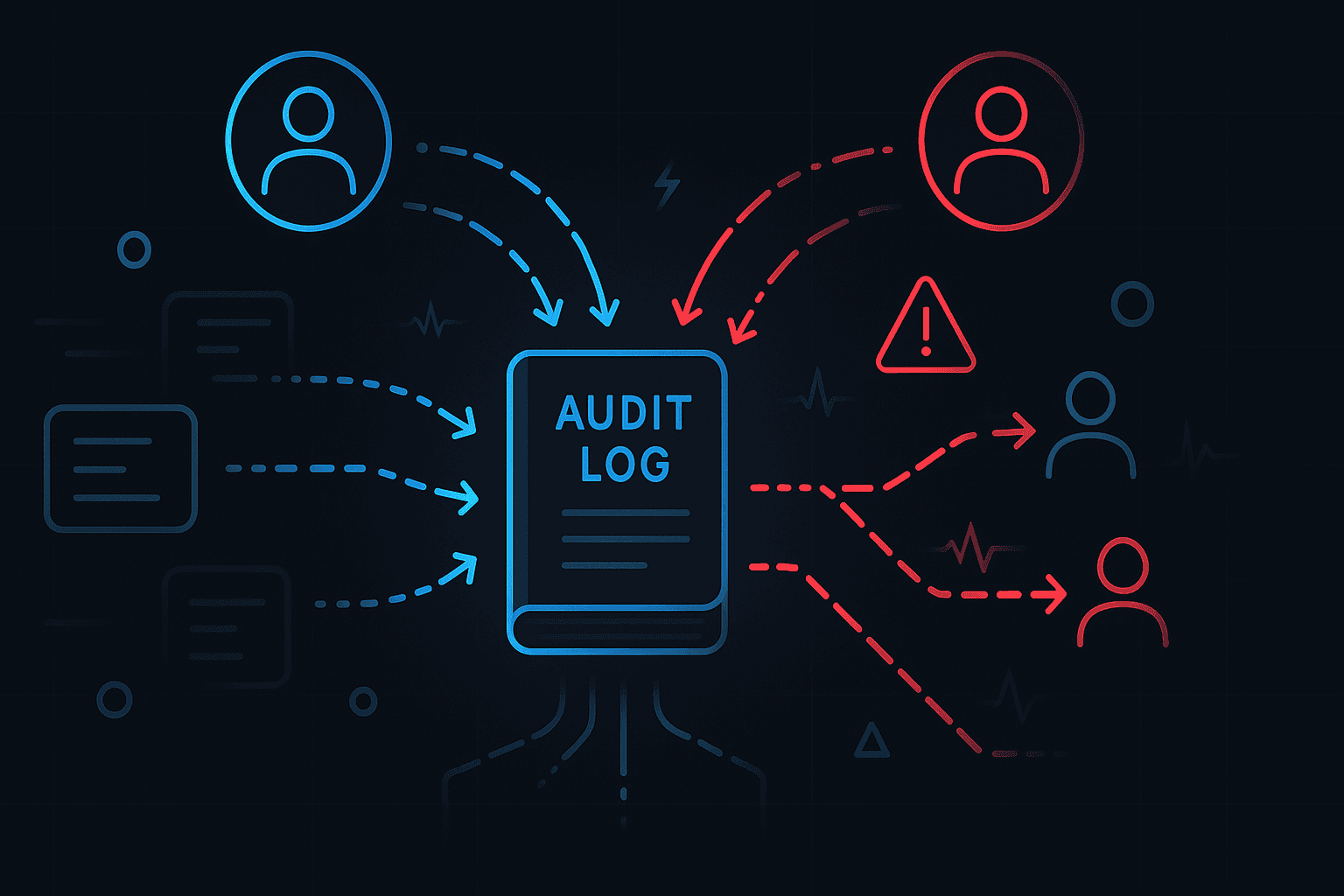
Auditors focus on accountability, traceability, and integrity. They do not care about stack traces or CPU metrics. They care about specific questions.
Who accessed sensitive data
Who changed a permission
Who exported a report
Who deleted a record
When did it happen
Where did it come from
Was it authorised
Is the record trustworthy
To answer these questions, regulators expect organisations to maintain structured, tamper evident records that reflect business level events. These records must be retained for a defined period, protected from modification, and available for inspection.
In short, they expect evidence, not logs.
The Characteristics of Compliance Ready Audit Records
A compliance ready audit trail has five essential properties.
1. Structure
Every event must follow a defined schema. Fields must be predictable and consistent. ISO 27001, SOC 2, and GDPR all emphasise structured logging for accountability.
2. Completeness
Events must capture important actions, not only technical details. This includes authentication events, configuration changes, data access, administrative actions, and policy modifications.
3. Integrity
Once recorded, events must be protected against tampering. This typically requires a chain of cryptographic hashes, digital signatures, or append only storage.
4. Context
Each event should include metadata such as actor identity, IP address, device information, and resource identifiers. Evidence without context is incomplete.
5. Retention
Evidence must be stored safely for years, depending on regulatory requirements. Logs rarely meet this requirement without additional tooling.
The first step in turning logs into evidence is normalisation. This requires mapping raw log lines into structured events. It begins with defining an event taxonomy.
An event taxonomy categorises events into types such as LoginEvent, PermissionChangeEvent, DataExportEvent, or CustomerRecordUpdateEvent. Each category has mandatory fields and an expected schema.
Once the taxonomy exists, a transformation pipeline can read raw logs and produce structured audit records. This pipeline typically performs:
Timestamp standardisation
JSON extraction or parsing
Actor identification
Resource mapping
Classification
Field normalisation
This process converts low level logs into meaningful business events.
Designing Evidence Transformation Pipelines
A typical pipeline involves the following stages.
Ingestion
Logs are collected from applications, servers, and cloud services. Ingested logs should be buffered to handle bursts and network variability.
Parsing
Logs are parsed using pattern matching, JSON extraction, regular expressions, or predefined log formats.
Normalisation
Parsed fields are transformed into a unified schema. This includes timestamp conversion, user ID mapping, and event type classification.
Enrichment
Events are enriched with additional metadata. For example, user role, IP geolocation, or resource ownership.
Validation
Events are validated against the taxonomy. Required fields must be present. Invalid events are quarantined.
Persistence
Validated events are written to an append only store with hash chain linking.
Indexing
Indexes are created for efficient querying by actor, resource, timestamp, and event type.
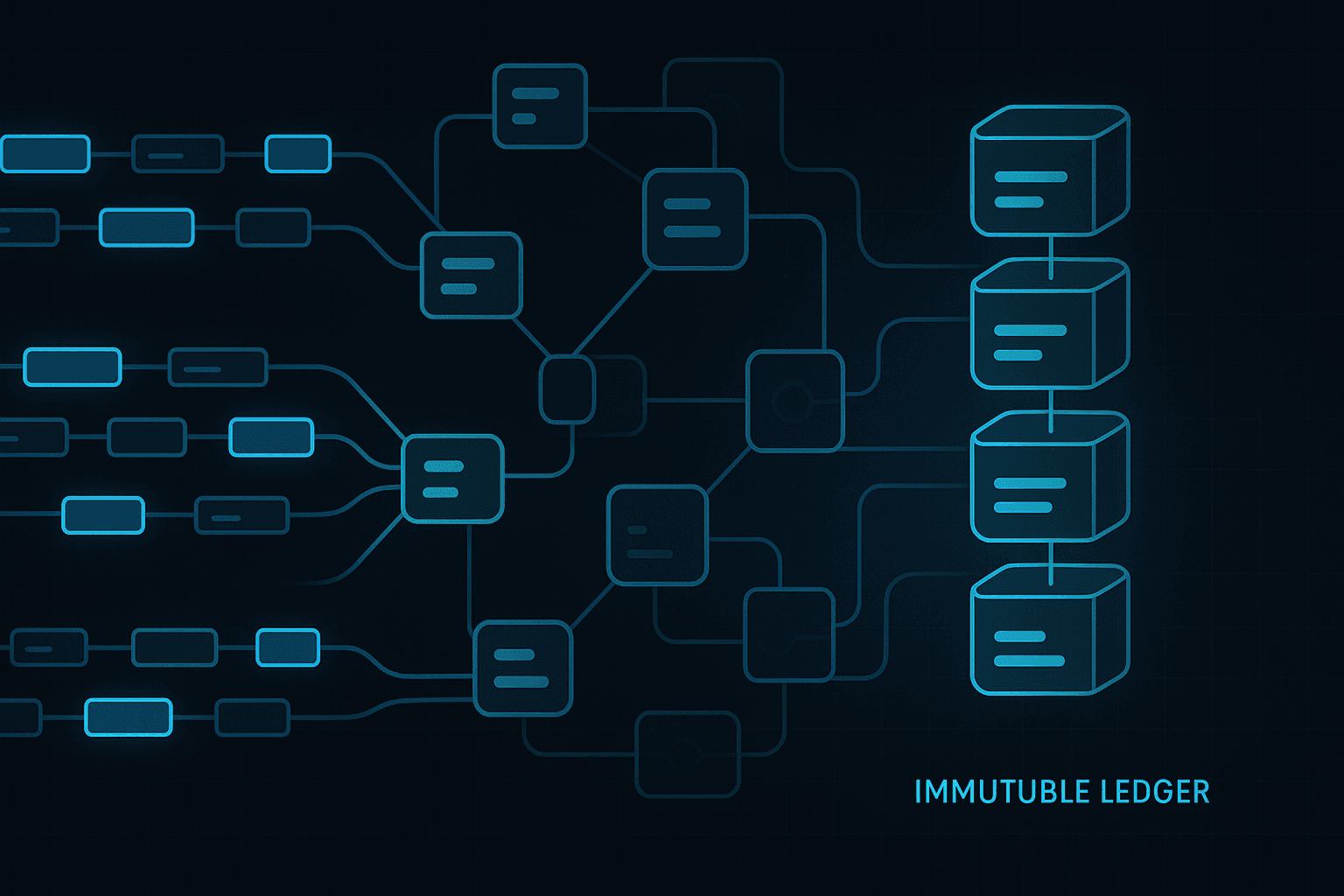
Immutability and Hash Chain Guarantees
Evidence is only useful if it can be trusted. Hash chains provide this trust. Each event contains a hash of its content and a hash of the previous event. This creates a chronological chain. If a historical event is modified or deleted, the chain breaks.
Hash based immutability gives regulators confidence that records have not been altered. This is a key requirement in SOC 2, ISO 27001, and GDPR.
When to Centralise Versus When to Distribute
Some systems collect all audit records in a central ledger. Others maintain per workspace, per project, or per tenant ledgers. The decision depends on:
Multi tenancy requirements
Data residency constraints
Query performance
Compliance isolation
Fault boundaries
Centralisation simplifies investigation. Distribution enhances privacy and isolation. Many platforms combine both.
Automating Compliance Reporting
Once a structured audit trail exists, compliance automation becomes possible. Reports for SOC 2, GDPR, HIPAA, and PCI DSS can be automatically generated. For example, a SOC 2 auditor may request:
All administrative changes over the past 90 days
All access to customer records
All permission changes by privileged users
All exports of sensitive data
A structured audit trail enables these reports to be generated instantly.
Building or Buying an Audit Trail Solution
Many teams try to build audit trail infrastructure internally. This is a significant undertaking. It requires expertise in cryptography, distributed systems, indexing, retention, and compliance. It also requires years of iteration.
Others adopt dedicated solutions that provide these features out of the box. This reduces time to value and improves confidence in the integrity of the evidence.
Conclusion
Logs are not evidence. They were not created to satisfy the demands of audits, investigations, or regulatory scrutiny. To convert logs into reliable evidence, organisations must apply structure, integrity, and context. They must adopt event taxonomies, transformation pipelines, and immutable storage.
Compliance ready evidence is not created by accident. It is created by design. Transforming logs into structured, immutable audit trails gives organisations the confidence they need to operate securely and meet regulatory expectations.