Designing Audit Trails for Multi Tenant SaaS Applications
Modern SaaS applications depend on clear accountability, secure data handling, and auditable histories of key user and system actions. This becomes significantly more complex in multi tenant architectures where multiple customers share infrastructure while expecting strict data isolation, privacy, and integrity guarantees. Designing an effective audit trail for multi tenant SaaS platforms requires far more than enabling verbose logging. It demands a structured, intentional approach to event modelling, tenant boundaries, hashing strategies, storage, and compliance.
This article explores how to design a production ready audit trail system for multi tenant environments. It covers tenant scoping, permissions, event separation, immutability, multi region concerns, retention planning, and the operational realities of scaling audit logging across many tenants.
The Nature of Multi Tenant Audit Trails
In a single tenant system, all events belong to one organisation and share a common namespace. Multi tenant systems differ fundamentally. One application instance may serve dozens, hundreds, or thousands of separate organisations. Each expects:
- strict isolation of their data
- visibility into only their own events
- clear, unambiguous identification of actors and resources
- tamper evident logging
- region specific storage policies if required by law
- consistent performance regardless of other tenants
Audit trails are the backbone of traceability in such systems. However, naive approaches, such as storing all events in a central table without tenant boundaries, quickly become brittle and risky. A secure design ensures that no tenant can retrieve or influence another tenant’s events, even indirectly.
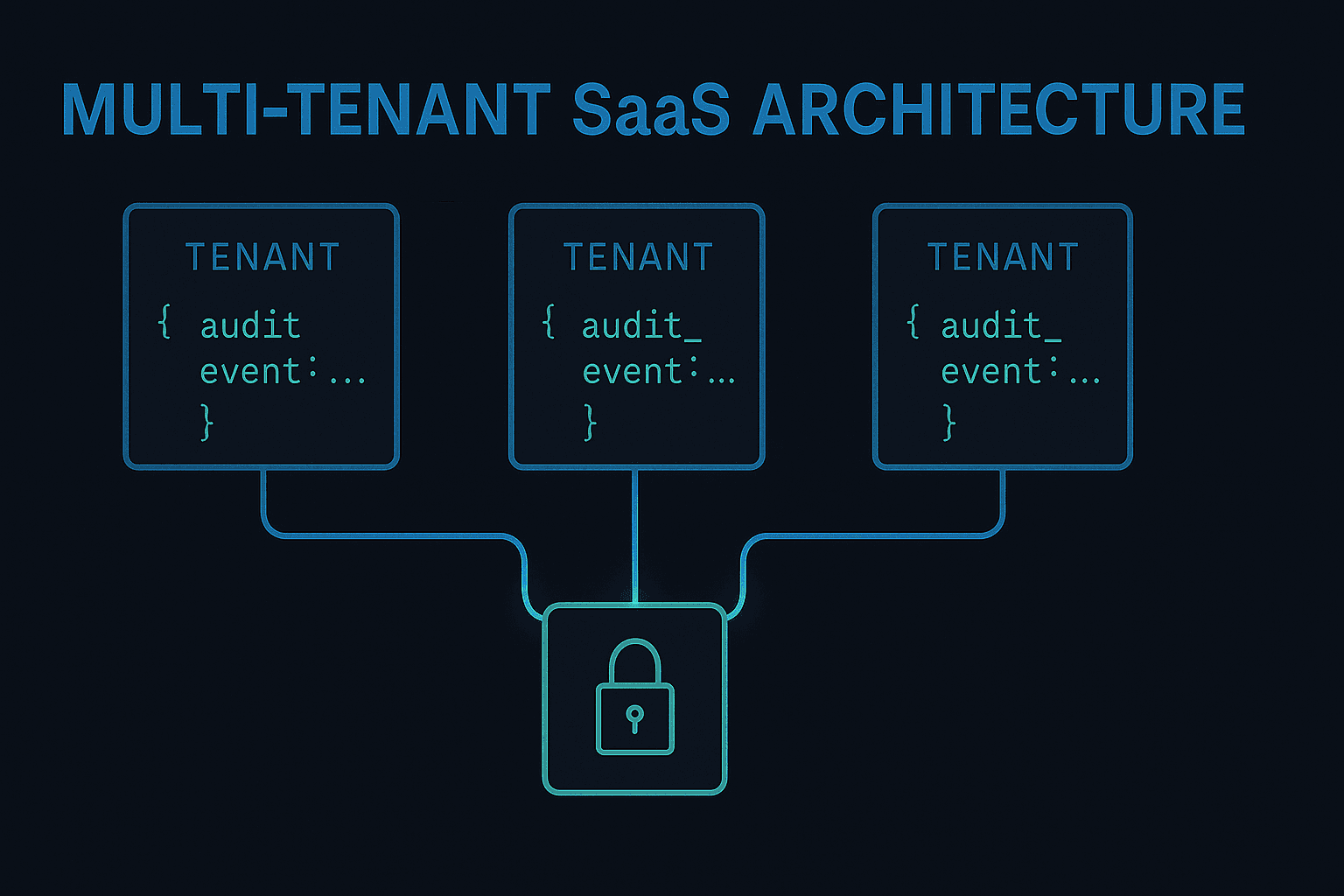
Designing for Tenant Isolation
Choosing a Tenant Identifier
Every audit event must include a tenant identifier. This ID should be:
- unique across all organisations
- immutable
- not derived from names or slugs
- securely generated
Using internal UUIDs rather than user facing identifiers prevents potential inference of other tenants.
Enforcing Tenant Isolation in Storage
There are three common patterns for storing multi tenant audit data:
-
Shared table with strict row level access control
All audit events are stored in one table with tenant_id as a partitioning key. Application logic must guarantee correct scoping on every query.
-
Logical separation using schemas or databases per tenant
Events for each tenant live in their own database or schema. This improves isolation but increases infrastructure complexity.
-
Dedicated storage per tenant
Audit events are completely separated at the storage layer, often needed for regulated environments.
Most SaaS platforms use the first approach because it balances scalability and manageability. However, careful attention must be paid to performance, indexing, and access controls.
Preventing Cross Tenant Leakage
Any query that fetches audit events must include tenant scoping. Relying on developers to consistently remember this is risky. Instead:
- enforce tenant scoping in the data layer
- ensure every query builder or ORM layer requires tenant_id
- test for cross tenant leakage using automated scenarios
- never allow cross tenant aggregation unless explicitly intended
Event Structure in Multi Tenant Systems
Every audit event should include enough information to represent actor, action, resource, and context. In multi tenant systems, there are additional considerations.
Required Fields
- tenant_id
- event_id
- timestamp
- actor_id
- actor_type (user, API key, system)
- action (string representing verb)
- resource_type and resource_id
- metadata for context
- previous_hash for immutability
- hash for current entry
Why Hash Chaining Matters More in Multi Tenant Architectures
Hash chains protect tenants from tampering, but they can also ensure:
- tenant specific chains do not affect other tenants
- the chain remains verifiable even when stored in one central table
- event ordering is clear within each tenant
- export operations yield verifiable histories
Each tenant should maintain its own hash chain. This prevents one tenant’s event volume from affecting verification of another tenant’s chain.
Handling Cross Tenant Actions
Some SaaS platforms have shared resources such as global settings, enterprise groups, marketplace apps, or administrative actions. These events require careful treatment.
Options:
- duplicate event to each relevant tenant’s chain
- publish event to a global chain separate from tenant chains
- tag event with multiple entities for contextual clarity
Selecting the correct approach depends on the need for audit export, compliance standards, and legal requirements.
Multi Region and Data Residency Considerations
Some regions enforce that audit data must remain within a specific jurisdiction. Multi tenant SaaS applications need region aware audit logging.
A region aware design includes:
- mapping tenants to regions
- ensuring events for a tenant always remain in their assigned region
- preventing logs from travelling across borders
- immutability chains maintained per region
If a tenant switches regions, a migration process must preserve chain integrity.
Retention and Archival Planning
Different tenants may have different retention requirements:
- financial services may require 7 years
- health data often requires long term retention
- consumer applications may require shorter periods to protect privacy
Retention should be configurable at the tenant level.
Archival strategies include:
- cold storage in object stores
- write once read many policies
- hashed snapshots to validate archives later
Query Performance and Indexing at Scale
Multi tenant audit logs often grow quickly. Performance challenges arise when:
- tenants generate high volume events
- queries must filter by tenant_id
- the system handles both hot and historical data
To maintain performance:
- partition by tenant_id and time
- index tenant_id, timestamp, action, and resource fields
- separate cold and hot data using storage tiers
- consider a search engine for dashboard queries
Exporting Per Tenant Histories
Tenants often need audit reports for:
- SOC 2 audits
- internal investigations
- compliance reviews
- regulatory requests
Exports should:
- include hash chain verification
- include export metadata
- include a verification file with chain roots
Conclusion
Designing audit trails for multi tenant SaaS applications is a complex but critical responsibility. A well designed audit layer provides security, transparency, and regulatory readiness at scale. With tenant aware hashing, strict isolation, region aware storage, and flexible retention policies, SaaS providers can deliver trustworthy audit capabilities to every customer.